Oracle Business Intelligence Vs Oracle Analytics Server
In the era of client-server computing, Oracle had the ad hoc reporting tool that was known as Oracle Discoverer. It
In the era of client-server computing, Oracle had the ad hoc reporting tool that was known as Oracle Discoverer. It

In this digital age, life is heavily dependent on semiconductors of one form or the other. From the time we
EXECUTIVE SUMMARY Wireless networks have been adopted for use both within organizations’ brick-and-mortar precincts and in many public areas like hotels, university campuses, modern city malls, homes, in airliners, and even in some public service vehicles. A way of integrating security within the wireless network infrastructure is therefore crucial to safeguard the data in motion…
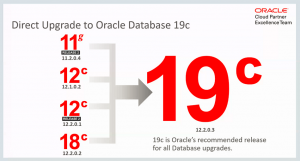
It is important for any organization that uses the Oracle database to understand its entitlements as well as its obligations

Oracle RMAN refers to the Oracle Recovery Manager, which is Oracle’s tool for performing database backup and recovery operations. Any

ASM is an acronym for Automatic Storage Management. ASM is the storage solution developed by Oracle for configuring and managing

Cloud computing is one of the new technologies that emerged in the first half of the decade between 2010 – 2020. As with all innovations, cloud computing borrowed heavily from computing practices and principles that were already in existence by then.

Our methodologies and tools of Systems Dynamics, Business Process Modelling and Operations Systems Management ensure that we capture all components of a Value Chain within an organization’s
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |